
We explain everything you need to know about privacy impact assessment, and how you can leverage it to assess potential privacy risk of new technology initiatives.
Technology Advisor | Cybersecurity EvangelistUpdated: June 27, 2021

Privacy is a well-recognized concept in many civilizations and cultures around the world. When something is private to a person, it usually means that something is intrinsically sensitive to them. It is a fundamental right, essential to the protection of human dignity and autonomy. Most people associate the term privacy with just digital privacy; however, according to Roger Clarke, privacy cuts across all facets of our lives including the privacy of the person (bodily privacy), the privacy of personal behavior (media privacy), the privacy of personal communications (interception privacy), and the privacy of personal data (data privacy).
In the digital age, the privacy landscape—the way in which privacy is protected and violated, has radically changed. Today, it has become far easier to collect, store, analyze, and share huge amounts of Personally Identifiable Information (PII) as has been demonstrated by big tech players in social media and search engines. The Internet has brought new concerns about privacy; now computers can permanently store records of everything. Assessing potential privacy risks has become more important than ever, and this is where the concept of Privacy Impact Assessment (PIA) comes into play.
A Privacy Impact Assessment (PIA) is a type of impact assessment conducted by an organization such as a government agency or corporation to determine the impact that a new technology project, initiatives or proposed programs and policies might have on the privacy of individuals. It sets out recommendations for managing, minimizing, or eliminating that impact. A key goal of the PIA is to effectively communicate the privacy risks of new technology initiatives. It also provides decision-makers with the information necessary to make informed policy decisions based on an understanding of the privacy risks and the options available for mitigating those risks.
PIA is very much similar in principle to the term Environmental Impact Assessment (EIA) where the environmental implications of a new project or plan are identified prior to the decision to move forward with the proposed action. Long before PIA became mainstream, Technology Assessment (TA) was used as a means of assessing and rating the societal impact of new technologies. As computing technology began to gain popularity in the 1990s, there became a need to measure the effectiveness of an organization’s data security and privacy risk of its systems, especially with most data now being stored on computers or other electronic platforms. This gave rise to the idea of Privacy Impact Assessment, and the methodology used by both TA and EIA inspired or formed the basis for the creation of the PIA.
PIA provides benefits to various stakeholders, including the initiating organization itself as well as its customers. PIA implementations can help build trust with stakeholders and the user community by demonstrating due diligence and compliance with privacy best practices. Privacy issues that are not adequately addressed can impact the community’s trust in an organization, project, or policy.
PIA provides a way for an organization to demonstrate commitment to, and respect for user privacy. Other key benefits include:
The very first step of the PIA process is to determine whether it is required. If an organization discovers that there is the potential that a project they are about to undertake has a high risk of impact on user privacy, it should carry out a privacy impact assessment. This will ensure that privacy risks and impacts that may be associated with the project are identified and mitigated.
So the question is: What exactly constitutes a high privacy risk project? Well, according to experts, one of the obvious signs to look out for in a project is if it involves a new or changed way of collecting, storing, analyzing, sharing, or destroying personal information. A project may be a high privacy risk if it involves new or changed ways of handling personal information that are likely to have a significant impact on user privacy. Determining whether a project meets this threshold requires a thorough understanding of all aspects of a project.
A threshold assessment is a preliminary assessment to help you determine if a project you are about to undertake could be a high privacy risk project, or has the potential to impact user privacy. This will give you an insight into the level of risk associated with the project. Of course, not every project will require a PIA. What a threshold assessment does is help unravel inherent privacy implications by looking out for factors that point to the potential for a high privacy risk, which will require a PIA to be conducted. These factors may include activities such as the collection of new or additional personal information, or actions that lead to an individual loss of control over their personal information. The consequences, including negative impacts on mental or digital wellbeing, could be significant for one individual, group of individuals, or the society at large—for example, increased facial recognition or biometric mass surveillance.
Once you have determined that a project portends high privacy risk to the user community, you should initiate a privacy impact assessment in accordance with the level of risk, to demonstrate commitment to and respect for user privacy. In fact, a PIA should be undertaken early enough in the project so that its findings can influence the overall design or outcome of the project. Failure to undertake a PIA at this point may expose your organization to risks such as privacy breaches, negative publicity, bad reputation, and user resentment, among others.

Several regulatory standards around the world including the EU GDPR mandate organizations to undertake PIA before embarking on any project that presents a specific privacy risk by virtue of its nature, scope, or purposes. The scale and complexity of your PIA will depend on the scale and complexity of your intended project. For complex projects, the PIA process and the resulting PIA report may contain more detailed and highly technical information. But due to the lack of a unified guideline on how to carry out such an assessment, most organizations processing personal data find it difficult to carry out a PIA.
| Features | ISO (International) | ICO (UK) | BSI RFID PIA (Germany) | IPC PbD (Canada) | HIQA (Ireland) | PIA Guide (US) | Privacy & Data PIA (EU) |
|---|---|---|---|---|---|---|---|
| Document Type | Framework | Guideline | Guideline | Framework | Guideline | Guideline | Framework |
| Target Audience | Organization processing personally identifiable information | Organization handling personal data | RFID operators | Organization processing personally identifiable information | Health and social care | SEC system owners and developers | RFID applications |
| Methodology | 4-phase PIA | 5-phase PIA | 6-phase PIA | Guided by the PbD principles | 4-phase PIA | 2-phase PIA | 6-step PIA |
Table 1.0 Comparison of PIA Frameworks and Guidelines
However, most Data Protection Authorities (DPAs) around the world such as the UK Information Commissioner’s Office (ICO), the Treasury Board of Canada Secretariat, and the International Organization for Standardization (ISO), among others have published high-level guidelines or frameworks that serve as a guide to conducting a successful PIA. Please see Table 1.0 above for a detailed comparison of some of the popular PIA frameworks and guidelines. The methodologies may vary, but the fundamental core components are similar. The PIA process from the various PIA frameworks and guidelines can be summarized in the following four core components:

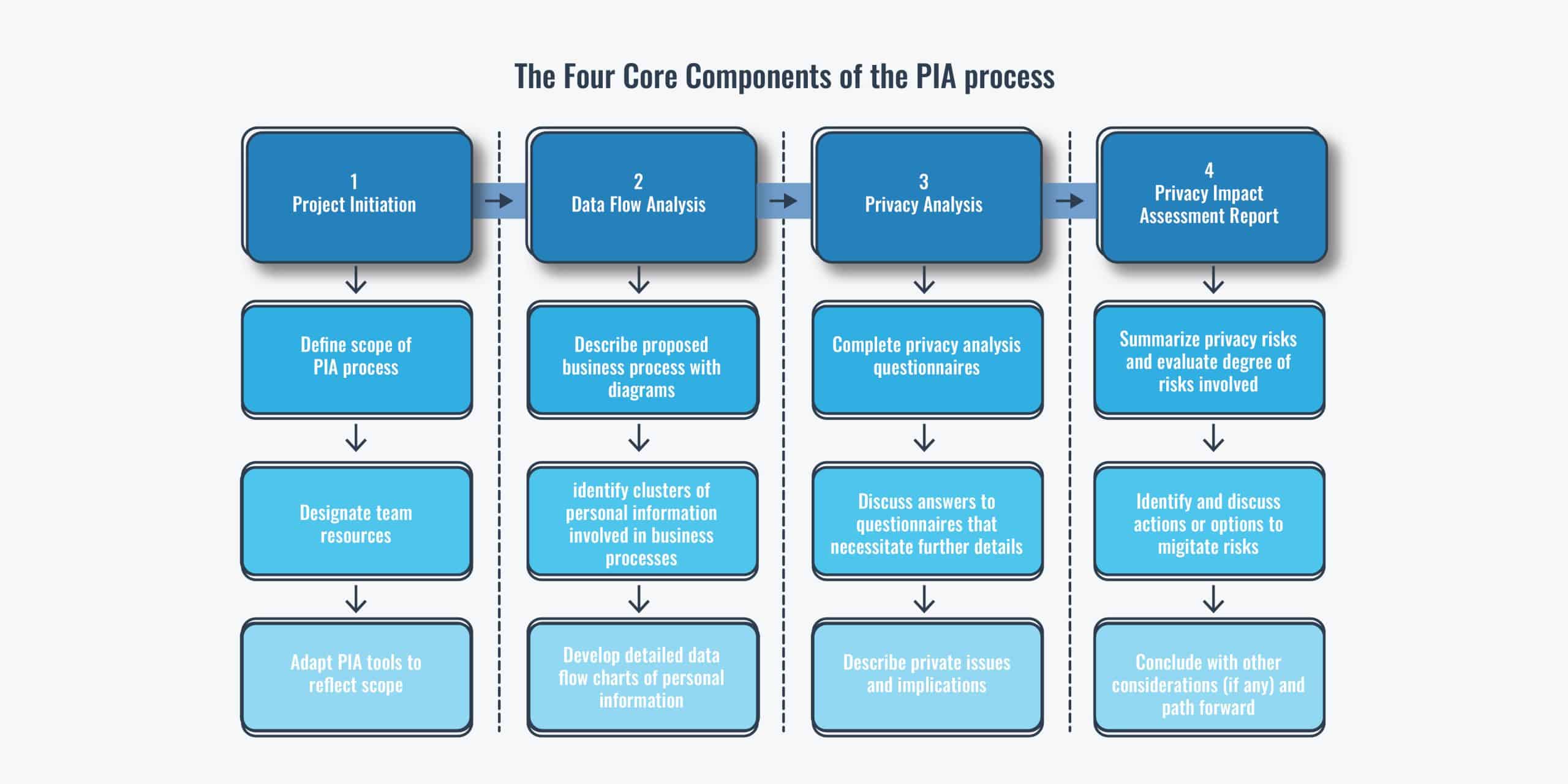
PIAs are only as good as the process (internal and/or external) that produces and supports them. This means that the right privacy culture, data privacy governance model, and the independence of the assessor must be fully guaranteed and embedded in the PIA process and the organization initiating it.
Here are some of the essential characteristics to look for in a good PIA:
It is important that actions are taken to implement the recommendations made in a PIA report. It can often be helpful to prepare a plan for implementing the recommendations including what actions need to be taken, roles and responsibilities, and time-frames.